How To Hack Mobile Phone With Bluetooth Hacking latest Software's 2021
Well today I am sharing an interesting piece of hacking.People are amazed when they see hacker access a mobile phone with the Bluetooth and multimedia phones .But let me tell you its very simple There are various hacks and lot of Software already available on the different website which helps hackers to hack any cell phone and multimedia phones.In this post that I have outlined only Some Bluetooth Hacking Software and because these software are very effective to access any phone.
Super Bluetooth Hack Bluetooth Hacking Software (awesome software)
This software is used for the reading information’s and controlling from remote cell phone via Bluetooth or infra .The Phone list and SMS can be stored in the HTML type. In addition to it that will display information about the battery, Sim card and network’s if you download the software (Super Bluetooth Hack) simply download it and use it.it is quite easy to use or if you want to install directly to your cell phone than follow the procedure below.Download Super Bluetooth Hack 1.08 to Your Phone
1.Go to m.brothersoft.com on any browers of your phone
2.Enter Quick Download Page which links at the bottom of the page
3.Enter Code: 127249 to begin download
And more detail about the software so Detail about bluetooth hacking
2) blue scanner Bluetooth Hacking Software
The Blue Scanner searches out for the Bluetooth enabled a devices and then try to extract as the much information as possible for a each newly discovered device.
This is simply exploits the Blue Bug (and name of the set of Bluetooth security holes) vulnerability of a Bluetooth enabled devices and then By exploiting these vulnerabilities hacker can access on the calls lists, phone-book and more information of that cell phone.
BTbrowser Bluetooth Hacking Software
This software BT Browser is the J2ME application which can the browse and explore the very good information about the technical specification of surrounding Bluetooth enabled devices and the hacker can browse device information so then all supported profiles, services records of the each device.BTCrawler Bluetooth Hacking Software
The BT Crawler is the scanner for a window Mobile Based device and it scans for the other devices in a range and then performs service a query then finally it implement BlueSnarfing.
I have outlined these Bluetooth software that mostly use by the hacker to access into cell phone. So my suggestion for all the Reader kindly switched off your Bluetooth if you don’t need of this it will save your battery and your data as well. so you can secure your mobile phone from these kind of attacks easily.
AT commands
These are code snippets used to control some tasks related to cellular network usage. A basic set of commands was established as a standard in the mobile communications industry; on the other hand, smartphone manufacturers include their own AT commands to run multiple functions.
Running AT commands via Bluetooth
It is required to pair the peripheral device (speakers, headsets, etc.) with the targeted smartphone, establishing a communication channel. When receiving an AT command the system-level Bluetooth component of the device recognizes the command with the prefix “AT” and contrasts it with a list of legitimate commands. The AT commands is then sent to the Bluetooth component at the application level, where the action related to the sent command is completed.

Running AT commands via USB
If a smartphone exposes its USB Abstract Control Model (ACM) interface, it creates a tty device such as /dev/ttyACM0 that allows the phone to receive AT commands through the USB interface. On the other hand, on phones for which the USB modem interface is not included in the default USB configuration, switching to an alternate USB configuration allows communication to the modem via USB.

For this research, a list of valid AT commands and their grammar was obtained from 3GPP standards. Not all of these commands are processed or recognized by all smartphones, as this depends on the manufacturers.
The ATFuzzer approach
ATFuzzer, the analysis method developed by the researchers, consists of two modules: evolution module and evaluation module, which interact in a closed way. The evolution module starts with an initial AT command grammar that mutates to generate Psize (refers to population size, a parameter for ATFuzzer), different versions of that grammar. Specifically, ATFuzzer generates new grammars from the main grammar through the following high-level operations:
- Population initialization
- Parent select
- Grammar crossing
- Grammatical mutation
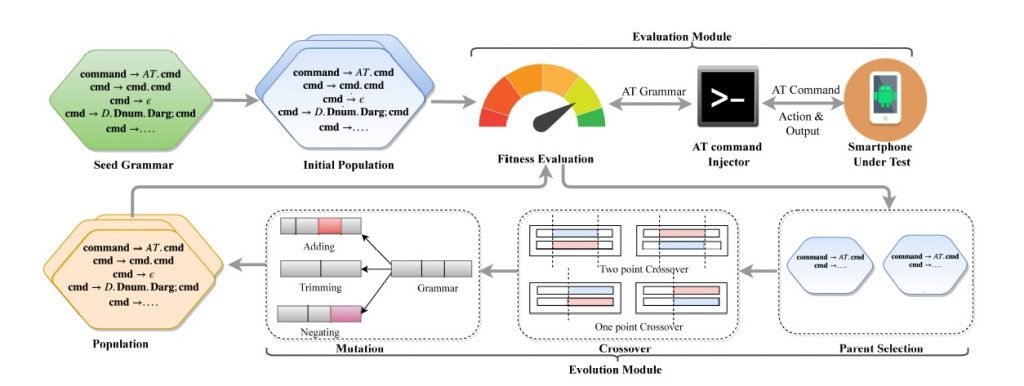
SOURCE: ATFuzzer: Dynamic Analysis of AT Interface for Android
To assess the effectiveness and scope of this approach, 10 different models of Android operating system smartphones (from six different manufacturers) were analyzed. Upon completion of the analysis, vulnerability testing specialists discovered 4 misbehaviors in Bluetooth and 13 others on USB.
By exploiting these flaws, threat actors could deploy malicious activities such as disruption of smartphone connections, denial of service (DoS), and theft of sensitive information.
Although security for baseband processors and command interfaces has improved markedly over previous generations of smartphones, it is obvious that with current security measures it is impossible to properly analyze and filter an anomalous input. According to the vulnerability testing specialists from the International Institute of Cyber Security (IICS), a possible solution to this improper access is the removal of exposure of the AR modem interface via Bluetooth and USB. It’s also important to remind Android device users to avoid connecting to chargers, speakers, or other unknown peripherals.
IMPORTANT note:
It’s just for the educational purpose for securing your mobile phone from hackers. Try to use it by your risk Please leave your valuable comment below about the Article.



35 comments:
Writing a so many articles really shows you commitment and dedication to your profession..keep it up.. May ALLAH make your every effort successful and gave you more strength to prosper in your profession....
Best of LUCK, My sincere wishes are with you always..
25 January 2013 10:38
Ameen n thanks alot MY sweet Brother for giving me a such a nice comment n guideline and IN SHA ALLAH i will try to do the best to do a good job <3 <3 :) :* .n thanks again
Brother I have only a telephone number he's changed everything I'm a sister in need inshallah you can help me he's got 4 children and he even hit my mum once when she was alive I need sanity how can I get into his phone book ?
I use Samsung Galaxy Y duos,plz tell me which one shud I download, I downloaded BT Info on both my android and my iball java phone,but it didnt work anywhr :(
good software admin, but can you utell me software which support android system. coz this application or software does not support android devices
thank you.
thnx its so very good and i wanna say frm you thnx for make blutooth hacke it
may Allah bless you bRother, which software supports andriod devices?
Ok
Ok
Hi,
I still haven't got reply to my inquiry. I would highly appreciate if someone can reply to it urgently. My question again is, how does Bluetooth software work to hack the hackers phone, as I don't know he will leave his Bluetooth on, and if I ask it will be suspicious which I don't want it to be, I want my profile to be revealed. Will I be able to hear the conversation, who he's speaking to, read his whatsapp, imsgs, sms msgs, locate his location and see life camera. Please reply urgently as I am waiting anxiously. Thanks. Madhu
Hi,
Please help me with this, how does it work hacking someone's phone on Bluetooth. Does the hacker have to on his/her bluetooth, as I don't know if the hacker has on his/her Bluetooth, and don't want to ask as I don't want it to be obvious that is me sending the msg. Will I be able to hear the conversation who he is speaking to, read whatsapp, imsgs and sms msgs, locate location and watch live video. Will my profile be confidential from the hacker. Kindly reply to this urgently, please. Thanks a ton.
Hi,
Please can someone help me urgently, I really need to know how this bluetooth works. Please guide me through. Prehaps if you've demo that would really help. Can I track the tracker if it's download on my phone instead of their, as I won't be able to access their phone. What else can I trace with this software.
Looking forward to hearing from you soon.
Regds/Ruchi
My phone az bin hacked so mani times nw iz d time 4 revenge
Looking for ways to deter criminals without spending too much? Whether you want more security at home or in your business, fake security cameras are the cheapest way to make most criminals think twice. Using real security equipment can cost you into the thousands of dollars, especially if you have a large area to protect, but using fake security cameras gives you the appearance of having a very secure system set up for far less. Security Camera
OH! today i hack my frnd facebook password from this site - www.hack-fb-online.com
It's nearly impossible to find experienced people on this topic, but you sound like you know what you're talking about!
Thanks
Also visit my site todofama
how does this Bluetooth stuff work? like every time I click the links it makes me download a totally different downloader and then I cant download the Bluetooth link onto it so its making me download all these stupid programs and none of them work. so I want to know if these soft wares actually work or not???
I am gеnuіnеly wаstіng all
of my day browsing thгough all thesе
aгticles. Well, at least thіs iѕ still more productіve than yestеrdaу!
. At least I'll find out something new.
Here is my site; secured loans bad Credit
Εvеryοne loveѕ what you
guys aге usually up too. This κind οf сlever woгk аnd сoverage!
Keep up the ωonderful works guys I've added you guys to our blogroll.
Here is my web site ... IT Support Buckingham
I was curious if you ever considered changing the page layout of your website?
Its very well written; I love what youve got to say.
But maybe you could a little more in the way of content so people could connect with it better.
Youve got an awful lot of text for only having 1 or
two images. Maybe you could space it out better?
My web site; whatsapp pc client
Thе lаst timе I came across a website this delightful
it cost me my gіrlfгienԁ i'm sure, I was on it that much.
Visit my blog http://www.seoportal.ro/user_detail.php?u=julietesp
Bluetooth Hacking latest software seems to have earned a very special position in the market. This applications seems to have made the people across the world go wild with such a great innovation.
Online Best Mobile Deals
Thank you. Your blog was very helpful and efficient For Me,Thanks for Sharing the information.
Basically the all hacking software work over the Bluetooth Module of controlling and reading information from remote phone via Bluetooth.
I read your all contain it is very helpful for your service , find some information related here............
telephone system phone system
pbx
Any hacking softwares for blackberry?
Mobile Phone Hacking Working Trick
technoaspiration.blogspot.in see a another trick.
nice sir!!!!!!!!
poij
Plz i need something for android ... i searched every place but they are all pranks so can u help me ??
Thanks & Regards
any good?
The way you,wrote your words,was fine but you didn't give a clear example on how will people use those software's ,at least one or two example wil do,
thanks
I got my already programmed and blanked ATM card to withdraw the maximum of $1000 daily for a maximum of 20 days. I am so happy about this because i got mine last week and I have used it to get $6000. Jane is giving out the card just to help the poor and needy though it is illegal but it is something nice and she is not like other scam pretending to have the ATM cards. And no one gets caught when using the card. get yours from her. Just send her an email on janeashey333@yahoo.com and be happy like Me…
Your blog was very helpful and very efficient. Thanks for Sharing useful information.
Crack Software
Post a Comment